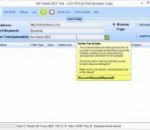
No Hands SEO tool is a very powerful backlink tool that helps to create relevant backlinks from 20 different platforms to help get all of your websites and web properties indexed quickly and ranking higher than ever, the best bit is it is all fully automated. Once you have entered in all of your websites you can simply click the "Go" button to create an endless supply of backlinks to your website 24 hours a day without you ever needing to attend it. While the No Hands SEO tool is fully automated you still have the option to get into the settings and configure the tool to only generate links with a certain PR, use proxies and all of the controls you expect from a great SEO tool in 2013 and then some. All searching for relevant targets, posting, link checking, pinging and otehr posting related jobs are fully automated for you by default so there really is minimal set up before you can start promoting your websites. There is a built in proxy harvester for use in the posting process which requires just 1 checkbox to enable. No Hands SEO backlink software is a fully automated tool that once setup will just run on and on creating you backlinks, SEO doesnt have to be hard ever again.
features: 1 Take photo by your webcam. 2 Processing your photos. There are 12 picture processing method. They are none, negatives,relief,Gray,Soften,Sharpen,Atomization,Lighting,RedBackground,GreenBackground,BlueBackground,Painting. 3 You can use this software to share these effects photos to your social networking site.
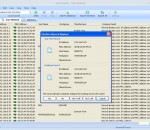
Trogon MAC Scanner is a necessary tool for efficient network administration and network maintaince. You will always know which computers and other network devices connected to the network, who are used them and where they are located. Trogon MAC Scanner automatic compare scan results with database and indicate new or changed hosts and you can immediately detect illegal access to the network. You can save scan results database to the file for future network monitoring and maintenance. Trogon MAC Scanner scan local network and detect IP addresses and MAC addresses for every network devices. Also find additional attributes: host name, workgroup, network adapter manufacturer. Trogon MAC Scanner use ARP protocol for scan subnet and use multithreading for simultaneous a large number of queries send out. This allows scan network incredible fast. If your computer connected with a several subnets, you can select any for scan. Features: Scan and list IP addresses and MAC addresses of all the network devices. Scan local network, find all network devices, detect their IP addresses and MAC addresses and list these addresses in pairs. Just a few seconds and you will get information about all connections to the network Save scan results into the database. After scan is finished you can add scan results to the database. When results has been added to the database you can edit records. Also the database will used for comparison with future scan results and detection new connections or any other changes in your subnet. Scan results can be saved for future reference and maintenance. Edit database records, add attributes (user name, location) to any record. When scan results has been added, you can add more details for any computer in the network. For every network device you can indicate where his physical location and who is his owner and any comments. Trogon MAC Scanner allows set attributes: host name, workgroup, user name, location, comments. It is enable to create new records manually (without scan) and change IP addresses and MAC addresses for an existed records. You will always have information for efficient network management about users and devices in your network. Automatic compare scan results with database records and indicate difference. Automatic comparison of the scan results and the database records indicate changes in your local network. You can immediately detect unauthorized IP addresses or MAC addresses modifications and illegal access to the network. Also you can always add new devices without manual addresses entering. Click record marked as changed and get comparison details contains databases and new addresses. Automatic addresses comparison always started after every scan. Export and Import database in file formats (txt, xml, csv). Trogon MAC Scanner can export scan results to the file (support formats are TXT, CSV, XML) for future usage and import records from file to the database. You can export some selected records or the entire database.
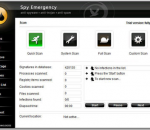
Spy Emergency is an anti-spyware software that fast and secure removes spyware and other internet infections from your computer. Spy Emergency protects you against spyware, adware, malware, homepage hijackers, remote administration tools, dialers, keyloggers, and many other types of internet infections. Spy Emergency supports resident shields for real-time protection and automatic infections database updates for better protection. Secure Your Ideas with Spy Emergency! Spy Emergency is a security application that protects your PC from spyware, malware and adware. FEATURES: · Built-in proactive resident shield protection with dynamic heuristic engine that can even detect new and unknown Internet threats · Lowlevel Anti-rootkit Protection · Site Identity Verifier · Extended behavioral heuristic scanning · Support for Internet Explorer, Mozilla Firefox and Opera browsers · Scan of your system memory · Scan of your registry · Scan of your storage · Built-in anti-spam · System directory storage scan · Tracking cookies scan · Host file scan · Hijackers scan · Heuristic malware detection · Polymorhic malware detection · Generic unpacker with support for UPX, Aspack, ... · Command line interface · Automatic LSP stack repair · Real-time memory shields that blocks spyware before it executes · Prevention shields that blocks malware installation · Browser shields, including homepage shield · Tracking cookies shields · Automatic incremental database updates · News updates · Individual items restore functionality · Keeplist · Scheduling support · Simple configuration · Intuitive and clear user interface for spyware removal · Handy Shell Extension Scanning · Skin support · Language support · Premium Technical support
Converts 32-bit Unicode codePoints to 16-bit surrogate pairs for Java String literals. It lets you enter String literals containing unsupported C-style Uxxxxxxxx escape sequences and it converts them to Java-supported surrogate pair escape sequences. You can also use the program without installing it at mindprod.com/jgloss/surrogatepair.html
BitNami Alfresco Stack greatly simplifies the deployment of Alfresco and its required dependencies. It can be deployed using a native installer, as a virtual machine or in the cloud. Alfresco is an Enterprise Content Management (ECM) system featuring Document Management, Web Content Management, Collaboration Management, Records Management and Image Management.
BitNami Drupal Stack greatly simplifies the deployment of Drupal and its required dependencies. It can be deployed using a native installer, as a virtual machine, in the cloud or as a module over an already installed infrastructure Stack. Drupal is a content management platform that allows an individual or community of users to easily publish, manage, and organize a wide variety of content on a website. In general, Drupal is used for community web portals, discussion sites, corporate web sites, intranet applications, personal web sites or blogs, aficionado sites, e-commerce applications, resource directories, and social networking sites. Drupal is easy to extend by plugging in one or more of the dozens of freely available modules.
For millions of men and women across the world, fishing is the number one way of escaping the hustle and bustle of hectic city life and the easiest way to get closer to nature. Unfortunately, most fishing fans simply don?t have time to make frequent and time-consuming long trips to their favorite destinations. If you are one of those people who get carried away whenever they see a turbulent river or a placid lake and you can?t wait to cast your lucky bait to land a trophy fish, indulge yourself to Fishing Simulator 2012! This great game features many picturesque fresh- and salt-water locations: from the emerald waters of the Carribbean seas to deep and silent Scottish lochs, from shallow mountain streams to giant reservoirs, from bottomless ponds to meandering rivers of the plains ? you have a whole world to see! You can enjoy each location at a different time of the day and use a wide variety of tackle according to the fishing conditions. No matter what kind of fish you want to catch ? from a tiny perch to a giant marlin ? it?s all there! The game offers an amazing level of detail ? both in terms of graphics and the realism of the fishing process ? and makes sure you will never 'come home' empty-handed. The relaxing soundtrack accompanying you throughout your fishing adventures and the quality of in-game graphics will be a pleasant surprise even for those users who have already tried several titles of the same kind. If you just love fishing in all of its forms and can?t afford frequent trips into the wild, get yourself a copy of Fishing Simulator 2012! Just start it, cast the bait into the water, think about something pleasant and wait for your biggest fish... After all, all fishing fans know that the time spent on fishing isn't counted into your age!
RogueKiller x64 is a useful application which will scan the running processes from your computer and kill those who are malicious. I developed this tool after seeing that some rogues (eg Security Tools) blocks the execution of disinfection programs, and some programs (eg rkill) appeared ineffective in killing the rogue process.
Altova MissionKit 2014 Enterprise Edition is a software development suite of industrial-strength XML, SQL, and UML tools for information architects and application developers. Altova MissionKit includes Altova XMLSpy, MapForce, StyleVision, UModel, and other market-leading products for building today’s real-world software solutions.
Having sailed for many days in search of a new home, the settlers came upon a lonely traveler who had become lost at sea. Thankful to the settlers for his rescue, the explorer decided to share a secret with them and unfolded an old map. It revealed three islands cloaked in mysterious fog that concealed hidden treasure and magic artifacts…
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.